In other words, it is how much people know about the cybersecurity threats they face, the risks that arise from them and the correct behaviors to adopt.
People, as users of IT systems, they are considered the weakest link and the main vulnerability of a computer system and technical security measures alone are not enough to protect it.
This is the reason why it is necessary to reduce the risk carried by the human element (end users) sensitizing him so that his will mature cyber awareness (Cyber Security Awareness) .
The first step is to share the scenarios of cyber risk in which the organization and its people work, illustrating the elements that compose them:
- Cyber threats
- The profiles and motivations of cyber attackers
- The risks of attack by the organization and possible consequences.
Cyber threats
Phishing:
phishing is a type of attack social engineering (Social Engineering) that attempts to trick victims into divulging sensitive information or unknowingly installing malicious software (Malware).
Cybercriminals use e-mail, social media, phone calls And text message (SMS) trying to pretend to be trusted interlocutors to manipulate their victim into performing a specific action: a click on a malicious link, the download an attachment, l?access to a counterfeit website or intentionally disclose sensitive information.
The information can then be used to access personal accounts or for?get hold? of their identity (identity theft).
Malware:
Malware is a type of malicious software designed to damage or enter a computer system without the user's knowledge.
Examples of malware are virus, worm, Trojan horses, spyware, adware And ransomware.
Malware is typically installed on a computer when a user clicks a link, downloads a malicious attachment, or launches a counterfeit software program.
Once installed, the malware can steal, delete or encrypt sensitive data.
It can also block the operation of the computer, the calculation functions making the system unusable.
Internal threat:
is a security threat that originates within an organization as opposed to that of one originating from? external.
It can be a current or former employee, a supplier or any other associated business that has access to the organization's data and information systems.
Internal attacks can be particularly dangerous because, unlike external actors who attempt to infiltrate a network, insiders typically have legitimate access to the information systems of the organization in which they operate.
Supply chain attacks:
an attack on supply chain (supply chain), also known as ?third party attack? attempts to harm an organization by exploiting its own vulnerabilities supply chain.
They are attacks that have the ability to infiltrate an entire network of organizations using a single compromise.
They are generally more difficult to detect than traditional malware attacks.
The profiles and motivations of cyber attackers
People involved in cybercrime are driven by different motivations, understanding them is important to take the right measures to counteract their actions.
These are the most frequent reasons.
Economic:
money is the biggest motivating factor for all criminal activity, and cybercrime is no exception.
These are thefts in the digital world that are much easier to carry out than a bank robbery.
Despite high-profile attacks on major organizations, the focus has shifted to small and medium-sized businesses (SMEs) Because I am ?prey? easier as they have weaker security measures.
It is more profitable for cybercrime to hit multiple small companies than a very large company that has invested millions to bolster its technological defenses.
Espionage:
Cyber attackers often use cyber espionage to steal confidential information, intellectual property or trade secrets.
Whether it's an attack on a nation (Nation State) or corporate espionage, espionage poses a significant threat to all organizations.
Breach after breach highlights how active attackers are in pursuing two particular sectors: politic And industrial.
Critical infrastructure how transport, water, telecommunications experience persistent attention from criminal organizations supported by their respective states (Nation State).
The use of the malware as a weapon by foreign Nation State organizations will affect all organizations except the largest ones that have invested adequate resources in cybersecurity, but the surprising fact is that the main facilitator of these attack vectors are people.
Social Engineering (Social Engineering) and inadequate security measures are the first areas a cybercriminal will try to exploit.
For this reason, it is crucial that organizations raise awareness among their staff (Cyber Security Awareness and Training) so that they are able to recognize these threats and defend themselves adequately.
Fun:
many hackers are motivated by the thrill and enthusiasm of infiltrating a company's computer system, if only to receive recognition from their peers (peers) of the hacker community.
Activism:
Activism is the act of violating (hack) a computer system or network with a political or social purpose.
Activism is a form of protest that has been around for a long time, the novelty is the all-pervading technology that can be used for hostile actions to certain? Targets? for ideological purposes.
One of the reasons for the increase in activism is that launching a cyber attack is cheaper than direct aggressive action.
Subtraction of resources:
stealing computational resources, or computing power, to produce bitcoins has become a profitable business
The mining of bitcoin reduces the functional performance of the computers of the? victims? and involves a significant consumption of electricity.
This type of attacker takes advantage of every opportunity, from private to multinational
Other:
this category includes insider threats such as unintentional data leaks, misconfigurations, user errors, and a host of other threats that are not dependent on targeted attack attempts by outsiders.
The most frequent causes of compromise are outdated software (Unpatched Software) and Social Engineering (Social Engineering) and pose the greatest risk to most organizations.
Risks of attack by the organization and possible consequences
What would happen if your organization was hacked?
What is the probability and what would the impact be?
To answer these questions, it is necessary to understand the uniqueness of the risk profile that the organization faces.
The extent to which cyber threats are dangerous to the organization determines the level of vulnerability that needs to be managed with mitigation plans and measures.
This is especially important for the personal and the supply chain because they are routes most used by malicious attackers.
The Training (Training)
A comprehensive cyber risk mitigation program for staff consists of the combination of three interventions:
- AWARENESS (AWARENESS),
- TRAINING,
- EDUCATION (EDUCATION).
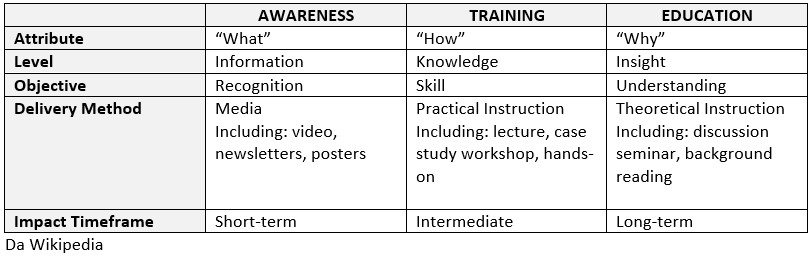
The awareness sessions (Awareness) are preparatory to training, their purpose is to enable people to recognize safety problems, assess their risks and act accordingly (e.g. not proceeding with a certain action, reporting a suspicious situation, etc.).
There Training (Training) is instead designed to give people the appropriate security skills and competences to act correctly (e.g. recognize a malicious link, a deceptive attachment, carry out an antivirus check, configure a security software, etc.)
The training program takes into account:
- the level of exposure to cyber risks
(e.g. privileged users, administration, executives are particularly exposed)
- the level of technical knowledge
(e.g. different contents for IT and Human Resources)
- the specific activities and tools used
(e.g. customer service, production, technical office)
to propose the most suitable and interesting contents.
The methods of providing the contents depend a lot on the characteristics of the company, but the general guideline is:
- short events,
- frequent,
- monothematic
- possibly interactive,
- frequent practical tests (e.g. phishing, malicious URLs, etc.)

